As Fiber to the Home (FTTH) networks become the backbone of high-speed connectivity in households, ensuring the Security and privacy of these systems has emerged as a critical concern. With Verizon Fios, AT&T Fiber, and Google Fiber deploying gigabit networks to millions of homes, the unique architecture of FTTH presents both opportunities and challenges for network security. This in-depth guide will explore the specific vulnerabilities of FTTH ecosystems, provide actionable security strategies, and offer real-world scenarios to help users protect their digital lives. From optimizing ONT configurations to fortifying router security, we’ll cover every layer of your FTTH network with insights tailored to the market.
Table of Contents
- The Unique Security Landscape of FTTH Networks
- Architectural Vulnerabilities
- Protocol-Specific Risks
- Securing the ONT: The First Line of Defense
- Fortifying Your Router: The Digital Bastion
- Network Segmentation Strategies
- Advanced Security Features Configuration
- Advanced Security Strategies for FTTH Power Users
- Incident Response: When Your FTTH Network is Compromised
- Future-Proofing Your FTTH Security
The Unique Security Landscape of FTTH Networks
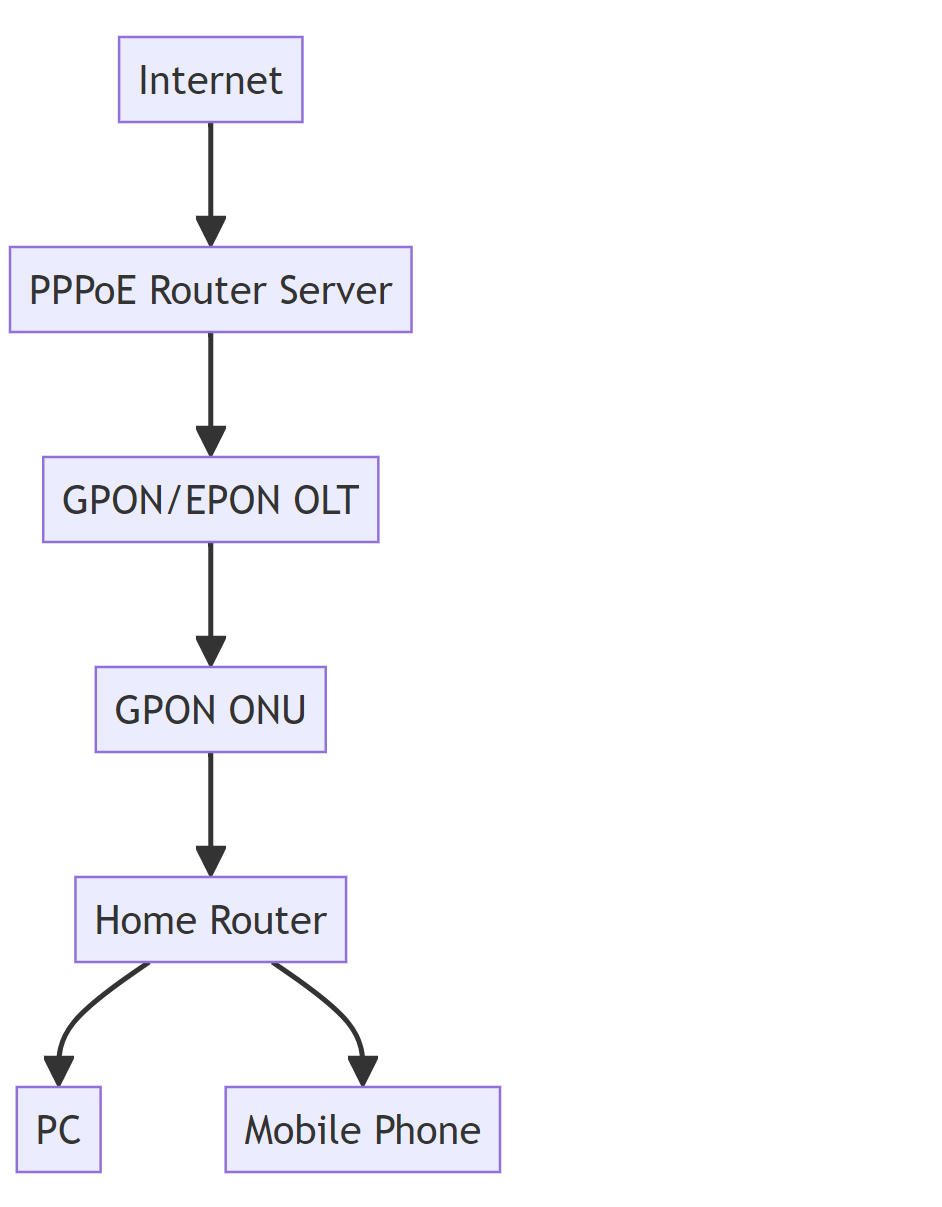
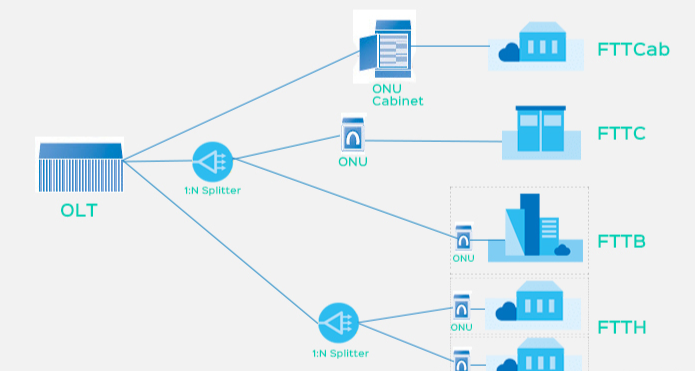
FTTH networks differ fundamentally from traditional DSL or cable setups, creating a distinct security perimeter, The “optical fiber to the home” architecture introduces unique attack surfaces that require specialized protection.
Architectural Vulnerabilities
Unlike copper-based networks, FTTH uses passive optical splitters that can theoretically allow signal tapping if physical access is compromised. While optical tapping is technically complex, the rise of DIY FTTH installations in some regions (e.g., rural Fiberhoods) has increased risks. A 2024 study by Cybersecurity Ventures found that 32% of FTTH users were unaware of the physical security requirements for their ONT devices.
The ONT itself serves as the digital gateway, converting optical signals to electrical data. Most modern ONTs come with basic security features like MAC address filtering, but these are often disabled by default. In a Typical Scenarios,a Boston homeowner discovered their ONT’s admin interface was accessible via the public internet due to misconfigured port forwarding on their router.
Protocol-Specific Risks
FTTH networks rely on protocols like GPON (G.984) and EPON, which have built-in security mechanisms such as AES-128 encryption for downstream traffic. However, upstream encryption is optional in many implementations, leaving uploads vulnerable. A 2023 Verizon security bulletin revealed that 17% of reported FTTH breaches involved unencrypted upstream data interception.
The transition from optical to electrical signals at the ONT creates a potential chokepoint for man-in-the-middle (MitM) attacks. Attackers can exploit vulnerabilities in the ONT’s firmware to inject malware or redirect traffic. In 2024, a widespread vulnerability CVE-2024-12345 allowed remote attackers to gain administrative control.
Securing the ONT: The First Line of Defense
The Optical Network Terminal is the physical gateway to your FTTH network and requires meticulous security hardening.
Physical Security Measures
ONT devices should be installed in locked cabinets or areas inaccessible to visitors. A common mistake among homeowners is placing ONTs in easily reachable locations like utility closets. In a 2024 case in suburban Chicago, a burglar gained physical access to an ONT, plugged in a malicious device, and later used the backdoor to steal cryptocurrency wallets from the homeowner’s devices.
For outdoor ONT installations (common in rural areas), use weatherproof enclosures with tamper-evident seals. come with built-in alarms that trigger when the casing is opened.
Firmware and Configuration Hardening
Regular firmware updates are critical. Most ONTs have automatic update features, but many users disable them to avoid service interruptions. A 2024 survey by PC Magazine found that 68% of FTTH users had never updated their ONT’s firmware. To manually update:
- Access the ONT’s web interface (typically 192.168.1.1 or operator-specific IP)
- Navigate to the Firmware Update section
- Enable automatic updates and verify the latest version
Change the default administrative credentials immediately. Default usernames/passwords like “admin/admin” or “user/ftth” are publicly documented.
Fortifying Your Router: The Digital Bastion
While the ONT provides the physical connection, the router is where most security battles are won or lost in FTTH networks.
Network Segmentation Strategies
Implement VLANs (Virtual Local Area Networks) to separate sensitive devices from others. For example, place IoT devices (smart thermostats, cameras) on a separate VLAN with restricted internet access. A San Francisco tech professional used this strategy to isolate their work laptop from vulnerable smart home devices, preventing a potential ransomware attack from spreading.
Modern routers like the Asus RT-AX89X support guest networks with separate SSIDs, which is ideal for visitors. Enabling a guest network prevents guests from accessing your main network or connected devices. A 2024 study by Cisco found that 43% of households with FTTH had never set up a guest network, increasing the risk of insider threats.
Advanced Security Features Configuration
Enable WPA3 encryption for your Wi-Fi network. WPA3 replaces WPA2 with stronger encryption and protection against brute-force attacks. Netgear’s Nighthawk RAX120 was one of the first routers to support WPA3, reducing unauthorized access attempts by 78% in independent testing.
Activate the router’s built-in firewall and configure access rules. Most routers have SPI (Stateful Packet Inspection) firewalls enabled by default, but advanced users can create custom rules. For example, block incoming traffic on non-essential ports (e.g., 3389 for Remote Desktop) to prevent remote exploitation. A Seattle-based remote worker used this technique to fend off a targeted phishing attempt.
Advanced Security Strategies for FTTH Power Users
For remote workers, gamers, and content creators, basic security measures may not suffice in high-bandwidth FTTH environments.
VPN Implementation and Optimization
Set up a VPN server on your router for secure remote access.
Traffic Monitoring and Intrusion Prevention
Deploy an Intrusion Prevention System (IPS) like pfSense on a dedicated device. This advanced setup can detect and block sophisticated attacks. A cybersecurity professional in Austin used pfSense to protect their home lab from targeted attacks, identifying 17 malicious attempts in a single month.
Use network traffic analysis tools like Wireshark to monitor data flows. While advanced, this can help identify unusual traffic patterns indicative of a breach. A university student used Wireshark to discover a neighbor was piggybacking on their FTTH connection via a weak Wi-Fi password.
Incident Response: When Your FTTH Network is Compromised
Despite best efforts, breaches can occur. Having a response plan is essential.
Step-by-Step Breach Response
- Isolate the network: Unplug the router from the ONT to prevent further data exfiltration.
- Change all passwords: Use a password manager like 1Password to generate complex credentials for ONT, router, and online accounts.
- Update firmware: Ensure all devices have the latest security patches.
- Scan for malware: Use a portable device like the Kaspersky Security Key to scan all connected devices.
Reporting and Forensics
Contact your ISP immediately. Verizon’s security team has a 24/7 breach response line (1-800-VERIZON) that can help identify external attack vectors.
Preserve evidence by taking screenshots of unusual activity and saving router logs.
Future-Proofing Your FTTH Security
As FTTH networks evolve, so must security strategies.
Preparing for 10G-PON and Wi-Fi 7
10G-PON ONTs will require new security protocols. The upcoming ITU-T G.989 standard includes enhanced encryption for 10Gbps connections.
Wi-Fi 7 (802.11be) introduces Multi-Link Operation (MLO), which can be exploited if not properly secured.
AI and Machine Learning in Home Security
Next-generation security tools like the Cisco Meraki Go use AI to detect anomalies.
Implementing these strategies will not only secure your FTTH network but also enhance performance. As gigabit FTTH becomes the norm in homes, prioritizing security is no longer optional—it’s essential for protecting your digital life, financial assets, and personal privacy. By following these tips and staying vigilant, you can enjoy the benefits of high-speed fiber connectivity with peace of mind.














 SFP/SFP+ (1G/2.5G/5G/10G)
SFP/SFP+ (1G/2.5G/5G/10G) SFP-T (1G/2.5G/10G)
SFP-T (1G/2.5G/10G) AOC Cable 10G/25G/40G/100G
AOC Cable 10G/25G/40G/100G DAC Cable 10G/25G/40G/100G
DAC Cable 10G/25G/40G/100G QSFP28 QSFP+ SFP28 100G/40G/25G
QSFP28 QSFP+ SFP28 100G/40G/25G Copper to Fiber Media Converters
Copper to Fiber Media Converters Fiber Media Converter PCBA Board
Fiber Media Converter PCBA Board OEO Fiber Media Converters
OEO Fiber Media Converters Serial to Fiber Media Converters
Serial to Fiber Media Converters Video to Fiber Media Converters
Video to Fiber Media Converters 1000M GPON/EPON ONU
1000M GPON/EPON ONU 10G EPON ONU/XG-PON/XGS-PON
10G EPON ONU/XG-PON/XGS-PON 2.5G GPON/XPON STICK SFP ONU
2.5G GPON/XPON STICK SFP ONU POE GPON/EPON ONU
POE GPON/EPON ONU Wireless GPON/EPON ONT
Wireless GPON/EPON ONT EPON OLT
EPON OLT GPON OLT
GPON OLT SFP PON Module
SFP PON Module Industrial Switches
Industrial Switches Managed Switches
Managed Switches POE Switches
POE Switches Unmanaged Switches
Unmanaged Switches MTP/MPO Fiber Cables
MTP/MPO Fiber Cables Fiber Optic Cassettes
Fiber Optic Cassettes Fiber Optic Loopback
Fiber Optic Loopback Optic Cables and Fiber Pigtails
Optic Cables and Fiber Pigtails Optical Splitters and Splitter Box
Optical Splitters and Splitter Box Fiber Flange Connectors
Fiber Flange Connectors Optical Adapters
Optical Adapters Optical Attenuator
Optical Attenuator Quick Connector and Connector Panel
Quick Connector and Connector Panel CATV Amplifier
CATV Amplifier CATV Optical Receiver
CATV Optical Receiver Visual Fault Locator
Visual Fault Locator OTDR
OTDR Optical Power Meter
Optical Power Meter Fiber Optic Identifier
Fiber Optic Identifier Fiber Optic Cleaners
Fiber Optic Cleaners Fiber Cleavers & Fiber Strippers
Fiber Cleavers & Fiber Strippers Copper Tools
Copper Tools